While working on a new website for a client, I sent a link for review as always. After seeing the new site (and loving it!) she said “but please take the ad off the website”. Well, there was no ad on the website, so I was pretty sure her computer browser had been infected with adware and/or spyware. Sure enough, after walking her through some anti-virus options and serious clean-up, she was able to see her new website in all its glory.
Are you seeing ads in strange places? The same ones over and over again? If so, you most likely have a malware problem.
If your computer is infected by malware, chances are, your antivirus has been disabled by the virus or trojan, your firewall if off, you’ve clicked a malicious link, or downloaded spyware along with other software.
Here’s some common symptoms to check:
Browser crashes & instabilities
- Browser closes unexpectedly or stops responding.
- Browser shows embedded ads on your website.
- The home page changes to a different Web site and cannot be reset.
- New toolbars are added to the browser.
- Clicking a link does not work or you are redirected to an unrelated Web site.
Poor system performance
- Internet connection stops unexpectedly.
- Computer stops responding or takes longer to start.
- Applications do not open or are blocked from downloading updates (especially security programs).
- New icons are added to desktop or suspicious programs are installed.
- Certain system settings or configuration options become unavailable.
Advertising
- Ads pop up even when the browser is not open.
- Browser opens automatically to display ads.
- New pages open in browser to display ads.
- Search results pages display only ads.
Types of Malware: Viruses, Trojans, Worms, and Bots
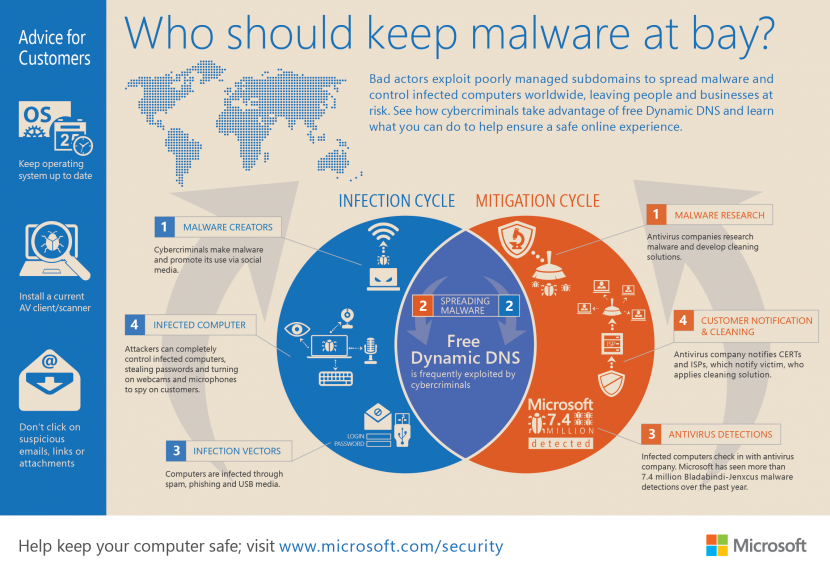
Viruses, worms, Trojans, and bots are all part of a class of software called malware. It’s code or software that is specifically designed to damage, disrupt, steal, or in general inflict some other “bad” or illegitimate action on computers, hosts, or networks.
There are many different classes of malware that have varying ways of infecting systems and propagating themselves. Malware can infect systems by being bundled with other programs or attached as macros to files. Others are installed by exploiting a known vulnerability in an operating system such as Windows, a network device, or other software, such as a hole in a browser that only requires users to visit a website to infect their computers. The vast majority, however, are installed by some action from a user, such as clicking an e-mail attachment or downloading a file from the Internet.
Some of the more commonly known types of malware are viruses, worms, Trojans, bots, back doors, spyware, and adware. Damage from malware varies from causing minor irritation (such as browser popup ads), to stealing confidential information or money, destroying data, and compromising and/or entirely disabling systems and networks. Malware cannot damage the physical hardware of systems and network equipment, but it can damage the data and software residing on the equipment. Malware should also not be confused with defective software, which is intended for legitimate purposes but has errors or bugs.
Two of the most common types of malware are viruses and worms. These types of programs are able to self-replicate and can spread copies of themselves, which might even be modified copies. To be classified as a virus or worm, malware must have the ability to propagate. The difference is that a worm operates more or less independently of other files, whereas a virus depends on a host program to spread itself.
Adware
Adware is a type of spyware program designed to display unsolicited advertisements, usually in the form of banners or pop-ups. Adware affects the Windows operating system. Fortunately, Microsoft is aware of this and has created a Malicious Software Removal Tool. This tool checks your computer for infection by specific, prevalent malicious software and helps to remove the infection if it is found. Microsoft will release an updated version of this tool on the second Tuesday of each month.
Adware is considered a legitimate alternative offered to consumers who do not wish to pay for software. Programs, games or utilities can be designed and distributed as freeware. Sometimes freeware blocks features and functions of the software until you pay to register it. So be very careful what you download and install on your computer. Oftentimes, adware is combined with Spyware.
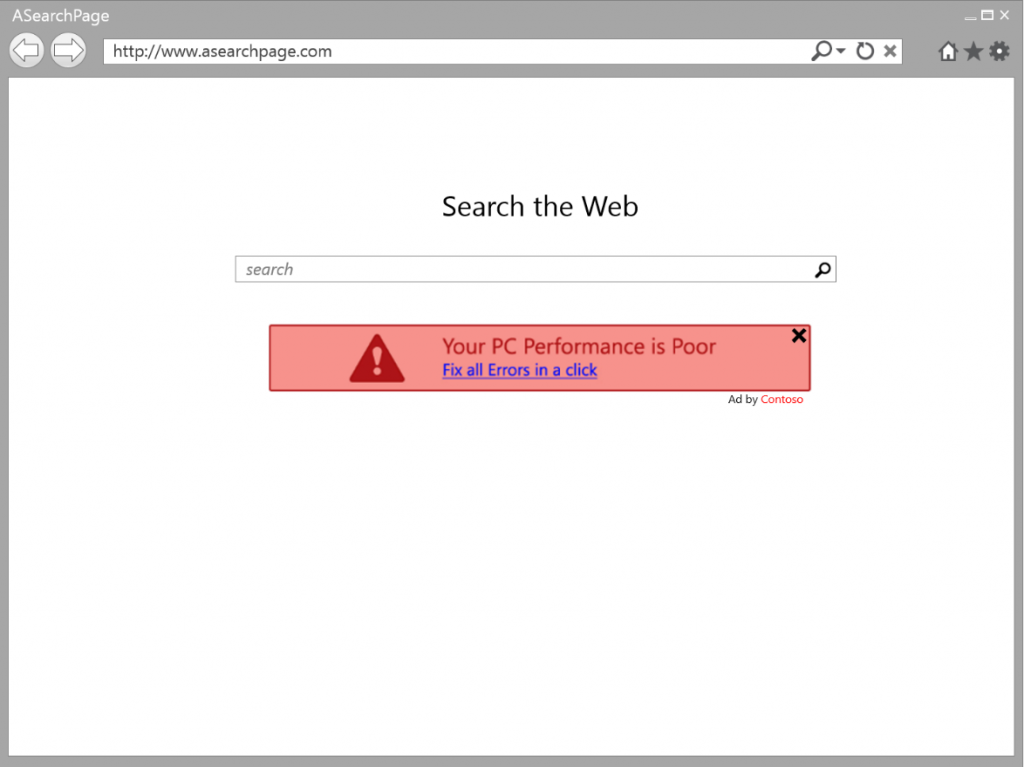
Spyware
Spyware is software that can install itself or run on your computer without providing you with adequate notice, consent, or control. Spyware might not display symptoms after it infects your computer, but many types of spyware or unwanted programs can affect how your computer runs. For example, spyware can monitor your online behavior or collect information about you (including personally identifiable or other sensitive information), change settings on your computer, or cause your computer to run slowly.
Viruses
A computer virus is a type of malware that propagates by inserting a copy of itself into and becoming part of another program. It spreads from one computer to another, leaving infections as it travels. Viruses can range in severity from causing mildly annoying effects to damaging data or software and causing denial-of-service (DoS) attacks.
Almost all viruses are attached to an executable file, which means the virus may exist on a system but will not be active or able to spread until a user runs or opens the malicious host file or program. When the host code is executed, the viral code is executed as well. Normally, the host program keeps functioning after it is infected by the virus. However, some viruses overwrite other programs with copies of themselves, which destroys the host program altogether.
Viruses spread when the software or document they are attached to is transferred from one computer to another using the network, a disk, file sharing, or infected e-mail attachments.
Worms
Computer worms are similar to viruses in that they replicate functional copies of themselves and can cause the same type of damage. In contrast to viruses, which require the spreading of an infected host file, worms are standalone software and do not require a host program or human help to propagate.
To spread, worms either exploit a vulnerability on the target system or use some kind of social engineering to trick users into executing them. A worm enters a computer through a vulnerability in the system and takes advantage of file-transport or information-transport features on the system, allowing it to travel unaided.
Trojans
A Trojan is another type of malware named after the wooden horse the Greeks used to infiltrate Troy. It is a harmful piece of software that looks legitimate. Users are typically tricked into loading and executing it on their systems. After it is activated, it can achieve any number of attacks on the host, from irritating the user (popping up windows or changing desktops) to damaging the host (deleting files, stealing data, or activating and spreading other malware, such as viruses). Trojans are also known to create back doors to give malicious users access to the system.
Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate. Trojans must spread through user interaction such as opening an e-mail attachment or downloading and running a file from the Internet.
Bots (BAD!)
Bots can be used for either good or malicious intent. A malicious bot is self-propagating malware designed to infect a host and connect back to a central server or servers that act as a command and control (C&C) center for an entire network of compromised devices, or “botnet.” With a botnet, attackers can launch broad-based, “remote-control,” flood-type attacks against their target(s).
In addition to the worm-like ability to self-propagate, bots can include the ability to log keystrokes, gather passwords, capture and analyze packets, gather financial information, launch DoS attacks, relay spam, and open back doors on the infected host. Bots have all the advantages of worms, but are generally much more versatile in their infection vector, and are often modified within hours of publication of a new exploit. They have been known to exploit back doors opened by worms and viruses, which allows them to access networks that have good perimeter control. Bots rarely announce their presence with high scan rates, which damage network infrastructure; instead they infect networks in a way that escapes immediate notice.
How to help prevent malware infection on your PC
Malware authors are always looking for new ways to infect your PC. Following the simple tips below can help you stay protected:
- Make sure your operating system is up to date
- Run up-to-date security software
- Get the latest software updates
- Understand how malware works
- Turn on your firewall
- Limit user privileges
- Use a PC cleaning utility to optimize performance and delete temporary files
The most important step to protecting your computer is to make sure that your OS is up to date. This means regularly applying the most recent patches and fixes recommended by the OS vendor – in my case Microsoft.
Secondly, you should have antivirus software installed on your system and download updates frequently to ensure that your software has the latest fixes for new viruses, worms, Trojans, and bots.
[x_alert heading=”What works for me?” type=”success”]For our Windows computers, we use Microsoft Security Essentials because it works quite well and is not near as bloated as other commercial security software – of which many actually add to the problem and often do not work!
I also recommend downloading and running Glary Utilities (free version is fine) each evening. Included among Glary’s tools are utilities for cleaning your Windows registry, deleting temporary files, and optimizing your computer.[/x_alert]
Additionally, you’ll want to make sure that your antivirus program can scan e-mail and files as they are downloaded from the Internet. This will help prevent malicious programs from reaching your computer.
Do you think your PC has a virus?
The Microsoft Safety Scanner is a free downloadable security tool that provides on-demand scanning and helps remove viruses, spyware, and other malicious software. Microsoft Safety Scanner expires 10 days after downloading. To re-run a scan with the latest anti-malware definitions, you can download and run Microsoft Safety Scanner again.
Chat LIVE with your questions – or simply use my contact form or email me. I look forward to learning more about you.
Cheers!
 Stacy Layman
Stacy Layman
Founder, Bright Green Path Web Solutions
Ocala, Florida